OAuth 2.0 : The Best Authentication and Authorization Technology

OAuth stands as a pivotal framework in modern web security, offering a robust method for authorization and then authentication. This article delves into the intricacies of OAuth 2.0, exploring its core components, functionality, and then implementation strategies. By understanding OAuth 2.0 comprehensively, organizations can also enhance their security protocols, streamline user access, and then ensure a seamless user experience.
Introduction to OAuth 2.0
OAuth 2.0 is an authorization framework that allows third-party applications to access user data without exposing user credentials. This protocol enables users to grant applications limited access to their resources, maintaining security and then privacy. OAuth 2.0 is a significant evolution from its predecessor, OAuth 1.0a, introducing simpler and then more secure methods for token-based authentication.
Core Concepts of OAuth 2.0
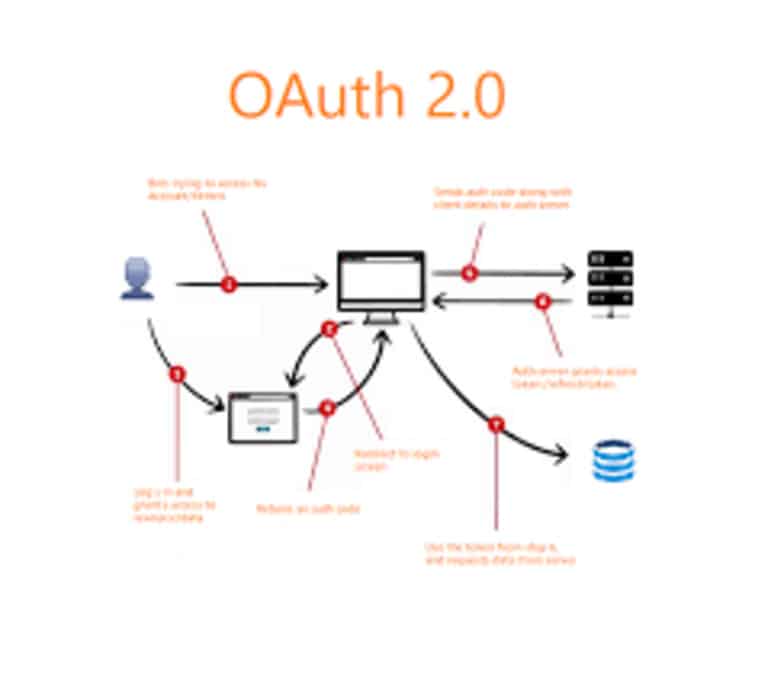
1. Authorization Grant Types
OAuth 2.0 defines several grant types, each suited for different scenarios:
Authorization Code Grant: This is the most common grant type, primarily used for server-side applications. To get an authorization code, you need to then exchanged for an access token, the user must be redirected to an authorization server.
Implicit Grant: Designed for client-side applications running in a browser, this grant type provides access tokens directly, bypassing the need for an authorization code. The authorization code grant is more secure than it. but simpler for single-page applications.
The grant gives the resource owner their password credentials.
The grant gives the resource owner their password credentials.
The user is given the information directly.It is less recommended due to security risks but can also be useful in certain scenarios.
Client Credentials Grant: This grant type is used for server-to-server communication, where the application authenticates itself rather than a user. It is ideal for backend services and then applications that do not involve user interaction.
2. OAuth 2.0 Roles
Understanding the key roles in OAuth 2.0 is crucial for implementing the framework effectively:
The person who allows access to and then owns the data is known as the resource owner.
Resource Server: OAuth 2.0 protects the user data hosted on the server.
Authorization Server: The server that grants access tokens following resource owner authentication andthen authorization acquisition.
Client: The application seeking access to the resource owner’s data, with the user’s consent.
3. Tokens
OAuth 2.0 utilizes various types of tokens to manage access:
Access Token: A token that allows access to protected resources. It usually doesn’t last long and then needs to be refilled on a regular basis.
Refresh Token: A token that can also be used to get a fresh access token once the one you have expires. The second version is less common in everyday English usage, but grammatically correct.)
ID Token: Used in Open ID Connect, an identity layer on top of OAuth 2.0, to provide information about the authenticated user.
OAuth 2.0 Flow
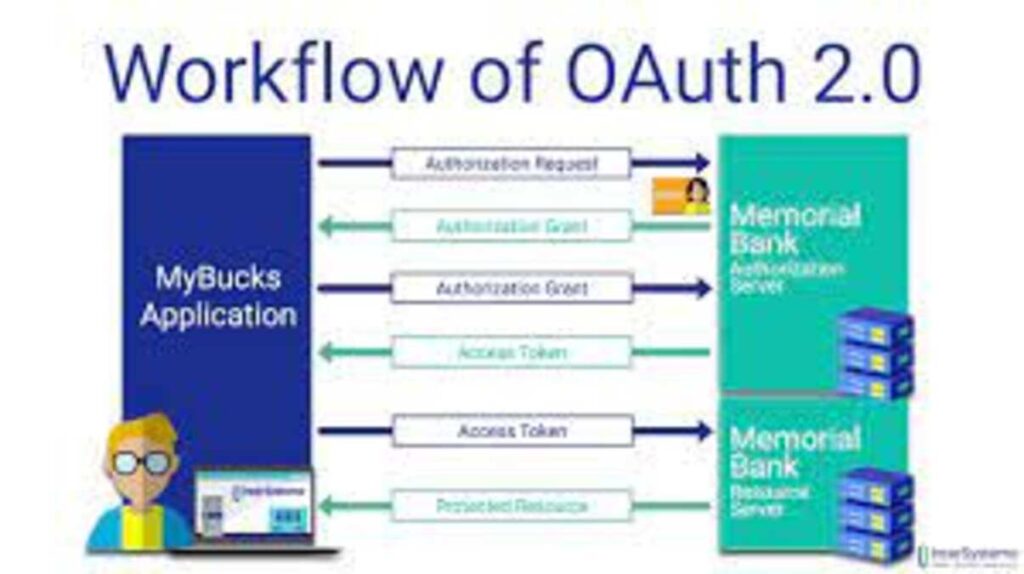
1. Authorization Code Flow
Applications with server-side components implement the Authorization Code Flow for authentication.
User Authorization: The authorization server requires the user to authenticate and grant access before redirecting them back.
Authorization Code: Upon successful authentication, the authorization server redirects the user back to the application with an authorization code.
Exchange of Tokens: The program swaps the authorization code for an optional refresh token as well as an access token.
2. Implicit Flow
The Implicit Flow is used for client-side applications:
User Authorization: The authorization server is accessed by the user.
Access Token: After authentication, the authorization server redirects the user back to the application with an access token in the URL fragment.
3. Resource Owner Password Credentials Flow
In this flow, the user’s credentials are directly provided to the application:
Credentials Submission: The user provides their username and then password to the application.
Token Request: The application sends a request to the authorization server with the user credentials.
Response Token: An access token is returned by the authorization server.
4. Client Credentials Flow
Used for server-to-server communication:
Token Request: The application authenticates itself with the authorization server using its client credentials.
Response Token: An access token is returned by the authorization server.
Implementing OAuth 2.0
1. Choosing the Right Grant Type
Selecting the appropriate grant type is essential for balancing security and then functionality. For server-side applications, the Authorization Code Grant is preferred. For client-side or mobile applications, consider the Implicit Grant or PKCE (Proof Key for Code Exchange) for enhanced security.
2. Secure Token Storage
Tokens must be securely stored to prevent unauthorized access. For web applications, store tokens in HTTP-only cookies or secure storage mechanisms. Mobile applications should use secure storage options provided by the operating system.
3. Token Expiration and Refresh
Implement mechanisms to handle token expiration and then refreshing. Access tokens should have a short lifespan, while refresh tokens can also be used to obtain new access tokens without requiring user interaction.
4. Protecting API Endpoints
Secure your API endpoints by validating access tokens on every request. Ensure that only authorized tokens with appropriate scopes can also access specific resources.
5. Implementing Scope and Consent
Define scopes to limit the access granted to the application. Scopes should be granular and then specific to the resources needed. Obtain user consent for the requested scopes to ensure transparency and then trust.
OAuth 2.0 Security Considerations
1. Preventing Token Leakage
Implement secure practices to prevent token leakage. Use HTTPS for all communications, avoid exposing tokens in URLs, and then ensure tokens are not stored in client-side storage accessible by malicious scripts.
2. Securing Authorization Codes
Authorization codes should be short-lived and used only once. Use the PKCE extension to mitigate the risk of code interception attacks.
3. Handling Refresh Tokens
Refresh tokens should be stored securely and then rotated regularly. Implement mechanisms to detect and handle cases of refresh token abuse.
4. Implementing Security Best Practices
Follow security best practices such as regular token revocation, implementing strong authentication mechanisms, and then monitoring for suspicious activities.
Common OAuth 2.0 Implementations
1. Google OAuth 2.0
Google OAuth 2.0 provides a seamless way for applications to integrate with Google services. It supports various grant types and then offers extensive documentation for implementation.
Read more: New Crypto Coins





